Ransomware-as-a-Service (RaaS) has established itself, sadly, as a viable sector. It would have achieved ‘unicorn’ status if it was a startup. RaaS is different. Cybercriminals are actively developing, and evolving malware designed to cause havoc, all for a subscription fee that ranges from month to month deals to a portion of successful extortion payments.
Cybercriminals with even the most elementary technical skills can deploy a ransomware attack with RaaS. The lucrative nature of RaaS as well as the difficulty in tracking down and prosecuting operators has led many security experts to believe this business model will continue to flourish in 2022.
RaaS has a Target Persona
If there is any doubt as to whether RaaS is an ‘ongoing concern’, one just needs to look at the playbook. A primary target or persona has been developed and shared by cyber criminals (Link) . That profile includes:
This playbook has been quite successful around the world in the last few years:
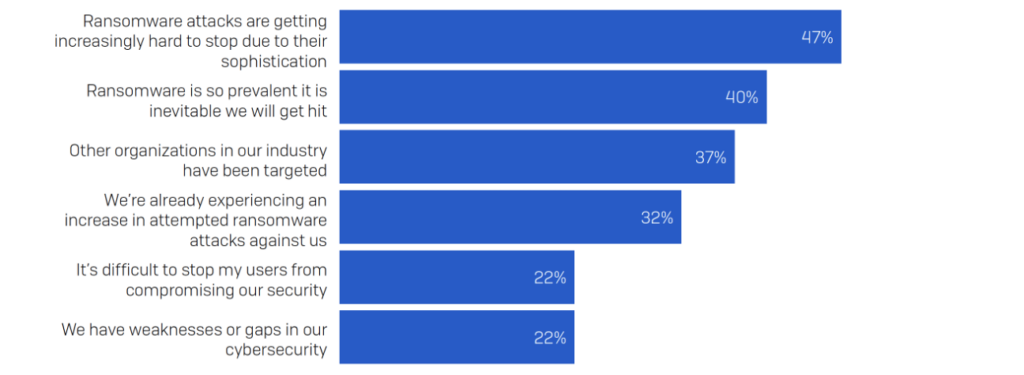
Leadership views cyber-based incidents as a top threat for 2022.
Cyber incidents ranked first in the Allianz Risk Barometer for only the second time in the survey’s history.
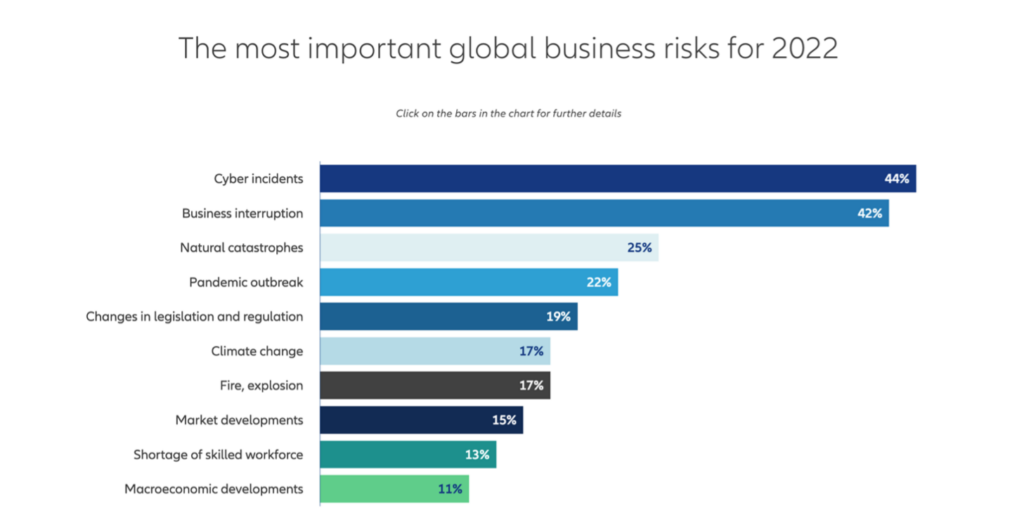
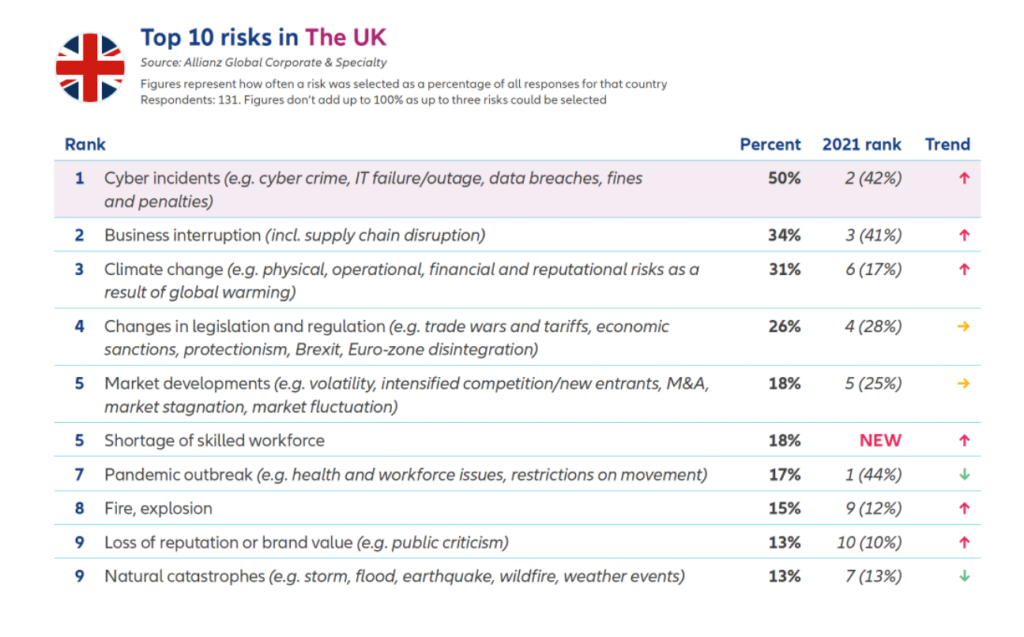
The concern in increases for United Kingdom leadership, whereby the threat of cyber incidents is on the minds of more senior leaders.
The Rise of Double Extortion: Attack Methods Are Evolving
Previously, ransomware was mainly accomplished through single extortion, whereby cybercriminals encrypt an organisation’s data and demand a ransom in exchange for a decryption key. Now, ransomware groups are exfiltrating victims’ data to an offsite location, then threatening to leak or publish the data if a ransom isn’t paid.
Data Leak Threats on the Rise
Previously, cyber-attacks were thwarted by using a backup to get its information back (if backup software was installed before the attack). Criminals are adapting to this by including a threat that not only encrypt stolen data, but sell it on the black market.
In 2021, 77% of ransomware attacks included a data leak threat, up 10% from 2020. (Link)
Ransom Demands Are Escalating
Increase attacks on Supply Chains
Instead of attacking a single victim, cyber criminals are thinking supply chains for one reason: impact. A prime example Kaseya attack in 2021, which impacted at least 1,500 of its managed service provider customers.
If organisations feel that an attack is inevitable, then the rate of success to recover should be of concern.
Data recovery after paying ransom
The answer is: Maybe
With the rise of attacks and their success rates, insurers have altered the clauses in their policies, thereby making it more difficult to depend on a payout to cover the costs in the future.
Boards are holding the C-Suite accountable for ransomware attacks, whereby 32% have been removed, either by dismissal or resignation, after a breach. (Cyberreason 2021)
For organisations, there is a material impact on being an on-going concern after an attack”
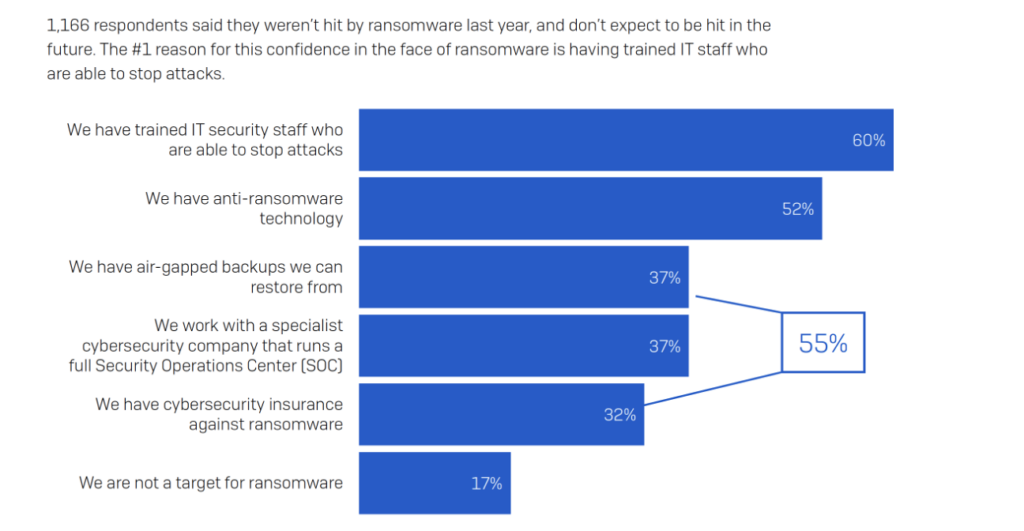
Ransomware is evolving at a rapid pace and will continue to impact all industries in 2022. What should be expected in the near and long term? Some predictions and trends to keep an eye on:
And lastly, perhaps the most eye-opening strategy: Pay to Stay Away?!?
Some cyber security leaders now believe that ransomware could evolve even further into a subscription-based model, in which Ransomware cyber criminals are paid to NOT target your organisation.
First, Learn from the Attack and Take Immediate Action!
In fact, an unnamed organisation that was the target of a successful ransomware attack and paid a ransom demand reported to be in the millions of dollars was apparently targeted in a SECOND ransomware attack by the same threat actors just 2 weeks later because they did not take the necessary steps to understand how the first attack happened or implement additional measures to assure the attack vector was remediated. (https://www.zdnet.com/article/ransomware-this-is-the-first-thing-you-should-think-about-if-you-fall-victim-to-an-attack/)
Top 5 Solutions Adopted After an Attack ( from cyber reason 2021 report )
Invest in Employee Education
Cybersecurity is ultimately a human problem and fostering internal awareness of how to identify a potential ransomware attack is a critical first line of defense for organisations. A threat can’t be avoided if it can’t be recognised. Educating your team on how to identify potential cyber threats can significantly reduce the chances of an attack. Investing in ongoing cybersecurity training should be a priority for organisations that want to become more cyber resilient.
West Lancashire Investment Centre
Maple View
White Moss Business Park
Skelmersdale
WN8 9TG
Registered address 10 Western Road Romford Essex England RM1 3JT Email: info@tes-es.com Tel: +44 (0) 1695-712664
| Thank you for Signing Up |


© Copyright 2012-2024 TES Enterprise Solutions Ltd (formerly Tectre Enterprise Solutions Ltd).
TES is registered in England and Wales.
Company number: 08308394. VAT registered number: 151 9903 03

